Master Risk Management in Operations for Business Resilience
Master Risk Management in Operations for Business Resilience
Learn effective risk management in operations. Discover key strategies to boost resilience and safeguard your business from disruptions.



When we talk about risk management in operations, we're really talking about the art and science of spotting, evaluating, and neutralizing threats that pop up in a company's everyday activities. It's not a dusty compliance binder on a shelf; it's a living, breathing strategy essential for survival and growth. At its core, it's about safeguarding the business from failures in its people, processes, and systems.
Why Operational Risk Management Is Mission-Critical
In today's fast-moving business world, you can't afford to treat operational risk as an afterthought. Strong risk management in operations isn't just a task for the compliance team—it's the bedrock that keeps a business stable when things get shaky.
Think of your company as a modern skyscraper. The shiny glass exterior gets all the attention, but its ability to survive a storm or an earthquake comes from the unseen structural supports and intelligent systems deep inside. Your operational processes are those hidden supports, and your risk controls are those smart systems.
When a disruption hits—a supply chain bottleneck, a critical system outage, or even a simple human error—a solid operational risk framework is what keeps a small problem from spiraling into a full-blown catastrophe. This forward-thinking approach is what truly separates the resilient organizations from the fragile ones.
Moving From Reactive to Proactive
Too many businesses only tackle risks after something has gone wrong. This reactive stance leads to expensive clean-ups, damaged reputations, and lost revenue. A proactive strategy completely flips that script. It’s about systematically hunting for vulnerabilities before they can cause harm, turning potential threats into a source of competitive advantage.
This shift in thinking is built on a few key principles:
Anticipating Failures: Instead of just waiting for things to break, you actively look for weak spots in your daily workflows.
Building Resilience: You design processes and systems with the built-in capacity to absorb shocks and keep running.
Fostering Awareness: Everyone, from the front lines to the C-suite, understands their part in spotting and managing risks.
When you adopt this mindset, you’re building a much more stable foundation for your company, freeing you up to focus on what matters most: growth and innovation. In fact, learning https://nolana.com/articles/how-to-improve-operational-efficiency is a natural result of getting serious about risk management.
An organization that masters operational risk management can adapt faster, recover quicker, and ultimately outperform competitors who are constantly fighting fires. It transforms risk from a liability into a strategic asset.
The business world is taking notice. The global risk management market was recently valued at around US$10.5 billion. Experts project it will more than double, hitting an estimated US$23.7 billion by 2028, which shows just how seriously modern companies are taking this discipline.
Before we get into the nuts and bolts, it helps to see the bigger picture. For a great primer on the fundamentals, check out this a complete guide to risk management.
The Four Pillars of Operational Risk

To get a real handle on operational risk, you first need to know where it comes from. Think of it like a building's foundation—everything rests on a few core supports. In this case, nearly every operational risk you can imagine traces back to one of four fundamental pillars: People, Processes, Systems, and External Events.
Having this framework in your back pocket gives you a powerful way to see and sort through potential problems in your own business. It stops being about vague worries and starts being about asking the right questions. Is this an issue of human error, a broken workflow, a tech glitch, or something completely outside our control? Finding the source is the first real step toward building a solid defense.
The Human Element
Your team is your biggest strength, but let's be honest, people can also be a major source of risk. This isn't about pointing fingers; it’s about recognizing that we're all human and mistakes happen. The risks in this category run the gamut from honest slip-ups to outright malicious acts.
It could be something as simple as a typo in a crucial financial report or a machine on the factory floor being set up incorrectly. These small errors can snowball into huge problems. On the darker end of the scale, you have things like internal fraud, where an employee knowingly abuses their position for personal gain. This pillar also covers issues like inadequate training or placing someone in a role without the right skills, both of which are recipes for trouble.
This is why insider risk is getting so much attention lately. In fact, nearly half (46%) of all organizations are planning to beef up their insider risk programs, worried about everything from data leaks to compliance failures. You can find more data on this trend in these risk management statistics.
Failures in Processes
Good processes are like the circulatory system of your business—they keep everything flowing smoothly. When those processes are poorly designed, outdated, or just plain ignored, they clog up the works and create massive operational risks. A process failure isn't a one-off mistake by a person or a computer; it's a systemic breakdown in how you get things done.
A few examples of process risks in the wild:
Badly Designed Workflows: An overly complicated approval process for invoices can delay payments, frustrating suppliers and hurting relationships.
Weak Quality Control: If a manufacturing line doesn't have the right checks and balances, faulty products can slip through and end up in customers' hands, leading to costly recalls and a tarnished reputation.
Poor Internal Controls: A classic example is when one person can both approve and send a payment. That’s a huge open door for fraud.
A broken process is like a leak in a pipe. You can keep mopping up the floor (fixing individual mistakes), but the real solution is to fix the pipe itself (the underlying process).
Breakdowns in Systems
In today’s world, technology is the backbone of just about every company. This pillar covers all the tech you rely on, from your core IT servers and networks to the specific software you use every day. When these systems go down, business often grinds to a halt.
Systemic risks can be dramatic, like a total server crash that takes your e-commerce site offline during Black Friday. But they can also be subtle and sinister. A bug in your analytics software might spit out bad data, leading your leadership team to make poor strategic choices. Issues with data integrity—where information gets corrupted or lost—can undermine everything from customer records to financial reports. This bucket includes everything from hardware failures and software bugs to security holes and telecom outages.
Unpredictable External Events
Finally, some of the trickiest risks are the ones that come from outside your four walls. You have very little, if any, direct control over these external events, but they can still wreak havoc on your operations, supply chains, and the market itself. You can't stop a hurricane, but good risk management in operations is all about being ready for one.
Common external risks include:
Natural Disasters: Things like floods, earthquakes, or wildfires can wipe out facilities and cripple logistics.
Supply Chain Shocks: The sudden failure of a critical supplier can bring your entire production line to a standstill.
Regulatory Changes: A new government regulation can force you to make expensive changes to your products or how you do business.
Political Instability: Trade wars, regional conflicts, or political turmoil can create a completely unpredictable environment.
To tie this all together, here’s a quick summary of the four pillars and what they look like in practice.
The Four Pillars of Operational Risk
Pillar | Description | Common Risk Examples |
|---|---|---|
People | Risks originating from human actions, whether intentional or unintentional. | Employee error, internal fraud, lack of training, unethical behavior, and skills gaps. |
Processes | Risks caused by failed or inadequate internal procedures, controls, and systems. | Poorly designed workflows, weak quality control, failed compliance, and lack of oversight. |
Systems | Risks arising from failures in technology, including hardware, software, and networks. | IT system outages, software bugs, data breaches, hardware failures, and cybersecurity attacks. |
External Events | Risks stemming from events outside the organization’s control. | Natural disasters, regulatory changes, supplier failures, political unrest, and economic downturns. |
By thinking about your operations through the lens of these four categories, you can start to systematically identify where your biggest vulnerabilities lie and build a more resilient business from the ground up.
Implementing the Operational Risk Management Lifecycle
Effective risk management isn't a one-and-done project. It’s a living, breathing cycle that constantly reinforces your operations.
Picture a ship captain navigating choppy seas. They don't just check the weather once and lock in a course. They're always on the lookout for potential storms, judging their severity, adjusting the sails, and keeping a close eye on the radar. That's how you should approach risk management in operations.
This cyclical method turns risk management from a theoretical exercise into a practical playbook. By moving through a structured lifecycle—Identification, Assessment, Mitigation, and Monitoring—you build a resilient system for handling whatever comes your way.
Stage 1: Identification – Uncovering Hidden Threats
You can't manage a risk you don't know exists. This first stage is all about proactive investigation—hunting for potential threats before they can cause any real damage. Think of it less like fortune-telling and more like detective work, using a few trusty tools to shine a light on vulnerabilities in your people, processes, and systems.
Here are a few practical ways to uncover these hidden risks:
Workshops and Brainstorming: Get teams from different departments in a room to talk through "what if" scenarios. You'd be surprised what comes to light when finance, IT, and production compare notes.
Process Mapping: Drawing out a workflow from start to finish is a fantastic way to spot bottlenecks, single points of failure, or gaps in your controls.
Incident Analysis: Dig into past failures and near-misses. They offer priceless clues about what can, and probably will, go wrong again if you don't address the root cause.
The goal here is to build a comprehensive risk register. This master list becomes the foundation for everything that follows.
Stage 2: Assessment – Prioritizing What Matters Most
With a long list of potential risks, the temptation is to tackle everything at once. That's a surefire path to getting overwhelmed. The assessment stage is where you bring order to the chaos by figuring out which risks truly deserve your attention.
The evaluation boils down to two simple questions:
Likelihood: How likely is this to actually happen?
Impact: If it does happen, how bad will the fallout be?
This infographic breaks down the core steps of a solid risk assessment, from gathering your intel to assigning a score.
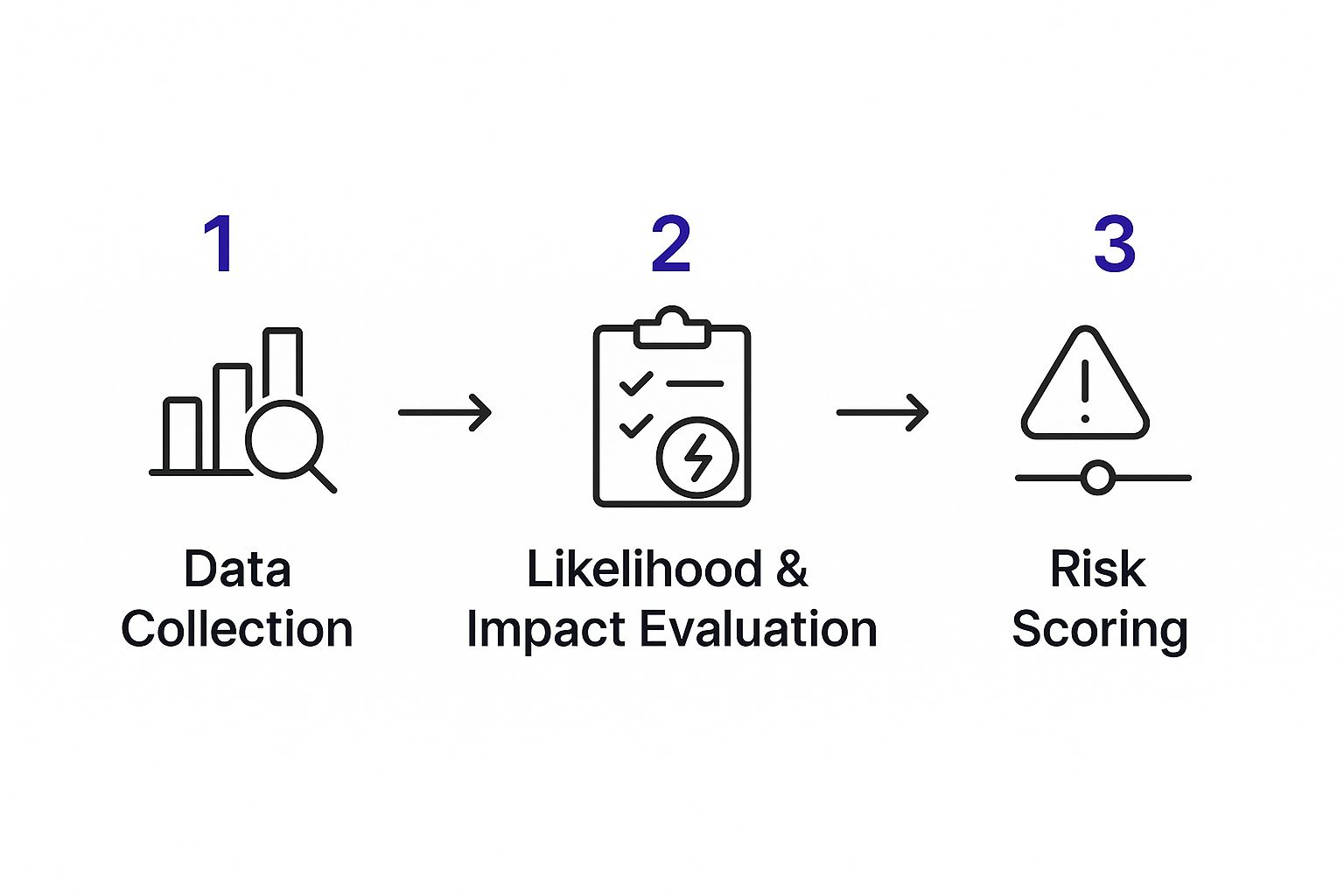
As you can see, it's a straightforward flow: data collection informs a careful evaluation, which leads to a clear risk score.
A go-to tool for this is a risk matrix. It's a simple grid that plots likelihood against impact. Anything that lands in the high-likelihood, high-impact corner (usually colored red) is an immediate priority. Risks in the low-low corner (green) can be managed with less urgency. To keep your analysis organized, you can use our risk assessment form template to guide you.
Stage 3: Mitigation – Crafting Your Response Plan
Okay, you've prioritized your risks. Now what? The mitigation stage is all about creating an action plan. This is where you develop and roll out strategies to control, reduce, or even eliminate the threats you’ve identified.
There are four main ways to respond to a risk, often called the "4 Ts":
Treat: This is the most common approach. You implement new controls or change a process to reduce the risk’s likelihood or impact. A classic example is installing backup generators to treat the risk of a power outage.
Tolerate: For some minor risks, the cost of fixing them might be higher than the potential damage. In these cases, you might consciously decide to accept the risk and just deal with it if it happens.
Transfer: This means shifting the financial hit of a risk to someone else. Buying insurance is the perfect example—you transfer the financial risk of a fire or flood to the insurance company.
Terminate: If a risk is just too big to treat, tolerate, or transfer, your best move might be to stop the activity causing it. This could mean shutting down a product line or pulling out of a particular market.
The right mitigation strategy depends entirely on the specific risk and your organization's comfort level with it. There’s no universal answer; the goal is to make a conscious, informed decision for each major threat.
Stage 4: Monitoring – Keeping a Watchful Eye
Finally, operational risk management is not a "set it and forget it" task. The monitoring stage is what makes the whole cycle work over the long term. Your business will change, new risks will pop up, and old ones will evolve.
Good monitoring involves tracking Key Risk Indicators (KRIs)—specific metrics that act as early warning signals. For instance, a KRI for a potential data breach could be an unusual spike in failed login attempts.
By keeping an eye on these KRIs, you can take action before a risk turns into a full-blown crisis. This final stage feeds right back into identification, creating a continuous loop of improvement that makes your organization stronger and more resilient over time.
Confronting Modern Threats to Your Operations

While the core principles of risk management haven't changed, the threats themselves certainly have. The risks that kept managers awake a decade ago feel almost quaint compared to what we're up against today. To build real resilience, your approach to risk management in operations has to tackle the high-stakes challenges of the modern business world head-on.
Two major threats have stormed from the periphery right to the center of operational risk: cyber attacks and geopolitical instability. These aren't just abstract concerns for the C-suite; they have a direct, and often devastating, impact on day-to-day business. The key is learning how to connect these massive trends to your reality on the ground.
Cyber Threats Are Core Operational Failures
For a long time, cybersecurity was seen as a problem for the IT department to sort out. That mindset isn't just outdated—it’s dangerous. Today, a cyber incident is a core operational failure.
Think of a ransomware attack not just as data being locked, but as a factory floor grinding to a halt because its control systems are paralyzed. When digital systems run everything from inventory to logistics, a digital threat becomes a very physical one. A successful cyberattack can do far more than steal data; it can cripple your ability to make your product, deliver your service, and keep your promises to customers.
A data breach isn't just an IT issue; it's a breakdown in the operational process of safeguarding company assets. A system outage isn't just a technical glitch; it's a direct disruption to your revenue-generating activities.
The scale of this challenge is enormous. In fact, for the fourth year in a row, cyber incidents—including ransomware, data breaches, and IT outages—are ranked as the top global business risk. These events cause severe operational disruptions and deep reputational damage. If you want to dive deeper, you can explore the full findings of the global risk report to see the data for yourself.
Navigating Geopolitical Instability
The second major modern threat is the ripple effect of geopolitical instability. In a globally connected economy, an event happening thousands of miles away can hit your operations like a tidal wave. Trade disputes, regional conflicts, and political polarization are no longer just news headlines; they are direct operational hurdles.
Just look at the real-world impacts:
Sudden Supply Chain Collapse: A trade dispute can trigger new tariffs or outright bans on critical components overnight. Suddenly, you're forced into a costly and chaotic scramble to re-engineer your entire supply chain.
Regulatory Whiplash: Shifting political alliances can create a constantly changing and unpredictable regulatory landscape. Compliance becomes a moving target, and the risk of penalties skyrockets.
Market Access Issues: Political instability can make it difficult or even impossible to operate in certain countries, cutting you off from both customers and suppliers.
Managing this kind of risk requires a new level of awareness and agility. It's about more than just having a few backup suppliers; it’s about understanding the political and economic currents that could disrupt your entire operational model. Teams need to be ready for sudden shocks and have contingency plans they can roll out at a moment's notice.
A well-documented response plan is your best defense against these unpredictable events. When a crisis hits, a clear protocol ensures a coordinated, effective response, minimizing chaos and downtime. You can get a head start by using a detailed crisis management report form template to structure your incident reporting from day one.
Ultimately, effective risk management in operations today means building a strategy that is both digitally fortified and globally aware. By recognizing that a server vulnerability is just as much a threat as a blocked shipping lane, you can develop an operational framework that’s truly ready for the challenges of this decade and beyond. This proactive stance is what separates the businesses that merely survive from those that truly thrive.
Building a Resilient Business Continuity Plan
When a crisis hits, you don't have time to figure things out. Strong risk management in operations isn't just about dodging bullets; it’s about making sure your business can take a punch, get back up, and keep moving forward. This is where a rock-solid business continuity plan (BCP) becomes your playbook for survival.
Lots of people mix up business continuity with disaster recovery, but they’re two different beasts serving two very different functions.
Disaster Recovery (DR) is the IT-focused part of the puzzle. It’s all about getting the tech back online—rebooting servers, restoring data from backups, and making sure the digital plumbing works again. Think of it as recovering your systems.
Business Continuity (BC) is the whole shebang. It’s about keeping the entire business operational. This means making sure your team can work, your supply chain hasn't ground to a halt, and your customers are still being served, even if your main office is a no-go zone. It's about recovering your business.
A great DR plan might get your website back up after it crashes, but a BCP is what ensures your support team can still take calls and your warehouse can still get products out the door.
Pinpointing Your Most Critical Functions
You can't save everything at once, so the first step in any good BCP is triage. You need to figure out what's absolutely essential. This is done through a Business Impact Analysis (BIA), which is a methodical way to identify your mission-critical operations and understand the real-world damage if they go dark.
A BIA forces you to ask the hard questions:
Which processes bring in the most money?
What operations are non-negotiable for keeping our promises to customers?
Are there any legal or regulatory lines we absolutely cannot cross?
Which functions are the dominoes that would topple other critical parts of the business?
By getting clear answers here, you can set your priorities straight. This is where you'll define a Recovery Time Objective (RTO)—the absolute maximum downtime a process can handle—and a Recovery Point Objective (RPO), which is the maximum amount of data you can afford to lose. This analysis becomes the bedrock of your entire continuity strategy.
A Business Impact Analysis transforms your BCP from a generic document into a precise, actionable roadmap. It tells you exactly what to save first when the fire alarm goes off.
The cost of being caught flat-footed is mind-boggling. The United Nations Office for Disaster Risk Reduction estimates that when you factor in all the knock-on economic effects and ecosystem damage, disaster-related costs now blow past $2.3 trillion annually. That figure is nearly ten times higher than the direct damage estimates we usually hear about. You can read more about the global impact of disasters on UNDRR.org.
From Analysis to Actionable Strategy
Once the BIA has shown you what's most important, it's time to build your playbook. This means creating detailed, step-by-step procedures that tell your teams exactly what to do during and after a major disruption. A good BCP isn't a high-level theory; it's a practical guide for when things get chaotic. For a nuts-and-bolts approach, check out this essential business continuity plan checklist.
Your plan needs to spell out everything from alternate work arrangements and communication plans for staff and stakeholders to the exact steps for firing up backup systems or moving to a secondary location. Documenting these processes is what ensures a coordinated, calm response in a high-stress moment. To make this documentation easier, you can use a structured framework like our business continuity plan form template.
We've seen how this pays off in the real world. When a massive earthquake struck Japan, one car manufacturer got its assembly lines running again far faster than its competitors. Why? Because their BCP included a deep, granular understanding of their entire supply chain, right down to the smallest component suppliers. While everyone else was scrambling to find new vendors, this company was already activating its pre-vetted alternatives, ultimately grabbing more market share.
It's a perfect example of how proactive planning doesn't just prevent a catastrophe—it can turn a crisis into a competitive edge.
Embedding Risk Management into Your Company Culture

You can have the most sophisticated frameworks and detailed playbooks for risk management in operations, but they’ll just gather dust if your company culture isn’t on board. Real operational resilience doesn't come from a new software tool or a binder on a shelf; it's born from making risk awareness a shared responsibility that’s woven into the fabric of every team.
This is about a fundamental shift in mindset. It’s about moving risk management from a siloed, top-down function to something everyone owns. When you empower every employee to see themselves as a risk manager in their own role, you create a powerful, organization-wide sensor network for potential threats.
Creating Clear Accountability
So, how do you make this happen without creating chaos? A proven approach is the "three lines of defense" model. It’s a simple but effective way to clarify who owns what, spreading accountability logically across the business.
Here’s how it breaks down:
First Line: This is your front line. It includes the operational managers and their teams who are hands-on with the processes every day. They own and manage risk as part of their job.
Second Line: Think of this as the support and oversight crew. It’s your dedicated risk management and compliance functions that provide the tools, expertise, and guidance for the first line.
Third Line: This is your independent check-and-balance. The internal audit team provides objective assurance that the first two lines are actually working as they should.
This model dismantles the dangerous assumption that risk is "someone else's problem." It embeds ownership directly into the day-to-day workflow where it matters most.
A proactive risk culture is the ultimate competitive advantage. It’s what allows a company to not just survive uncertainty but to adapt and even thrive by making smarter, more informed decisions at every level.
Fostering a Proactive Environment
Building this culture really boils down to two things: ongoing training and transparent communication. Training can’t be a one-and-done annual presentation; it needs to be practical, role-specific, and continuous. And communication must be open and blame-free. People have to feel safe raising their hand to flag a potential issue without fear of reprisal.
Despite the obvious benefits, getting this cultural piece right is where many organizations fall short. A shocking 87% of risk professionals feel that risk management processes are not widely accepted within their companies, according to research shared by ProcurementTactics.com. That statistic reveals a huge gap between policy and practice.
Ultimately, a company that truly values proactive risk management is one that empowers its people. When your team is trained, accountable, and engaged, they become your single greatest asset in building a resilient operation. For companies looking to bring in the right leaders, an operational risk manager job application template can be a great starting point to define the skills that really matter.
Frequently Asked Questions
What Is the First Step in an Operational Risk Program?
The very first move—before you even think about frameworks or tools—is to get executive sponsorship. Without leadership championing the effort, any risk program is dead in the water. Once you have that backing, assemble a team with people from different departments.
With your team in place, your next step is a high-level Business Impact Analysis (BIA). This helps you pinpoint the most critical processes that keep your business running. Focusing here first gets you early wins and proves the program's value to everyone else.
How Does Operational Risk Differ from Financial Risk?
Think of it this way: financial risk is about the money itself—things like credit defaults, market swings, or currency fluctuations. Risk management in operations, on the other hand, deals with the engine that makes the money: your internal processes, people, and systems.
A bad investment is a financial risk. The entire trading platform crashing because of a server failure or a sleepy employee hitting the wrong button? That's a classic operational risk. While the outcome is often financial, the cause is a breakdown in how the business runs.
Understanding the distinction is key. Financial risk is about managing capital, while operational risk is about managing the machinery that generates that capital. One cannot be effective without the other.
How Often Should We Review Our Risk Assessments?
Risk assessments aren't a "set it and forget it" activity. A good rule of thumb is to conduct a full, formal review at least annually.
But don't wait a whole year for your biggest threats. Your risk register and the plans for mitigating your most severe risks should get a closer look, probably quarterly.
And remember, major business changes should always trigger an immediate review. If you’re launching a new product line, expanding to a new country, or rolling out a new ERP system, you need to assess the new operational risks that come with it right away.
Ready to transform your risk management from a static process into an intelligent, autonomous workflow? Nolana deploys AI agents that can plan, execute, and detect risks across your operations. Discover how our platform can give you unparalleled visibility and control. Learn more at https://nolana.com.
When we talk about risk management in operations, we're really talking about the art and science of spotting, evaluating, and neutralizing threats that pop up in a company's everyday activities. It's not a dusty compliance binder on a shelf; it's a living, breathing strategy essential for survival and growth. At its core, it's about safeguarding the business from failures in its people, processes, and systems.
Why Operational Risk Management Is Mission-Critical
In today's fast-moving business world, you can't afford to treat operational risk as an afterthought. Strong risk management in operations isn't just a task for the compliance team—it's the bedrock that keeps a business stable when things get shaky.
Think of your company as a modern skyscraper. The shiny glass exterior gets all the attention, but its ability to survive a storm or an earthquake comes from the unseen structural supports and intelligent systems deep inside. Your operational processes are those hidden supports, and your risk controls are those smart systems.
When a disruption hits—a supply chain bottleneck, a critical system outage, or even a simple human error—a solid operational risk framework is what keeps a small problem from spiraling into a full-blown catastrophe. This forward-thinking approach is what truly separates the resilient organizations from the fragile ones.
Moving From Reactive to Proactive
Too many businesses only tackle risks after something has gone wrong. This reactive stance leads to expensive clean-ups, damaged reputations, and lost revenue. A proactive strategy completely flips that script. It’s about systematically hunting for vulnerabilities before they can cause harm, turning potential threats into a source of competitive advantage.
This shift in thinking is built on a few key principles:
Anticipating Failures: Instead of just waiting for things to break, you actively look for weak spots in your daily workflows.
Building Resilience: You design processes and systems with the built-in capacity to absorb shocks and keep running.
Fostering Awareness: Everyone, from the front lines to the C-suite, understands their part in spotting and managing risks.
When you adopt this mindset, you’re building a much more stable foundation for your company, freeing you up to focus on what matters most: growth and innovation. In fact, learning https://nolana.com/articles/how-to-improve-operational-efficiency is a natural result of getting serious about risk management.
An organization that masters operational risk management can adapt faster, recover quicker, and ultimately outperform competitors who are constantly fighting fires. It transforms risk from a liability into a strategic asset.
The business world is taking notice. The global risk management market was recently valued at around US$10.5 billion. Experts project it will more than double, hitting an estimated US$23.7 billion by 2028, which shows just how seriously modern companies are taking this discipline.
Before we get into the nuts and bolts, it helps to see the bigger picture. For a great primer on the fundamentals, check out this a complete guide to risk management.
The Four Pillars of Operational Risk

To get a real handle on operational risk, you first need to know where it comes from. Think of it like a building's foundation—everything rests on a few core supports. In this case, nearly every operational risk you can imagine traces back to one of four fundamental pillars: People, Processes, Systems, and External Events.
Having this framework in your back pocket gives you a powerful way to see and sort through potential problems in your own business. It stops being about vague worries and starts being about asking the right questions. Is this an issue of human error, a broken workflow, a tech glitch, or something completely outside our control? Finding the source is the first real step toward building a solid defense.
The Human Element
Your team is your biggest strength, but let's be honest, people can also be a major source of risk. This isn't about pointing fingers; it’s about recognizing that we're all human and mistakes happen. The risks in this category run the gamut from honest slip-ups to outright malicious acts.
It could be something as simple as a typo in a crucial financial report or a machine on the factory floor being set up incorrectly. These small errors can snowball into huge problems. On the darker end of the scale, you have things like internal fraud, where an employee knowingly abuses their position for personal gain. This pillar also covers issues like inadequate training or placing someone in a role without the right skills, both of which are recipes for trouble.
This is why insider risk is getting so much attention lately. In fact, nearly half (46%) of all organizations are planning to beef up their insider risk programs, worried about everything from data leaks to compliance failures. You can find more data on this trend in these risk management statistics.
Failures in Processes
Good processes are like the circulatory system of your business—they keep everything flowing smoothly. When those processes are poorly designed, outdated, or just plain ignored, they clog up the works and create massive operational risks. A process failure isn't a one-off mistake by a person or a computer; it's a systemic breakdown in how you get things done.
A few examples of process risks in the wild:
Badly Designed Workflows: An overly complicated approval process for invoices can delay payments, frustrating suppliers and hurting relationships.
Weak Quality Control: If a manufacturing line doesn't have the right checks and balances, faulty products can slip through and end up in customers' hands, leading to costly recalls and a tarnished reputation.
Poor Internal Controls: A classic example is when one person can both approve and send a payment. That’s a huge open door for fraud.
A broken process is like a leak in a pipe. You can keep mopping up the floor (fixing individual mistakes), but the real solution is to fix the pipe itself (the underlying process).
Breakdowns in Systems
In today’s world, technology is the backbone of just about every company. This pillar covers all the tech you rely on, from your core IT servers and networks to the specific software you use every day. When these systems go down, business often grinds to a halt.
Systemic risks can be dramatic, like a total server crash that takes your e-commerce site offline during Black Friday. But they can also be subtle and sinister. A bug in your analytics software might spit out bad data, leading your leadership team to make poor strategic choices. Issues with data integrity—where information gets corrupted or lost—can undermine everything from customer records to financial reports. This bucket includes everything from hardware failures and software bugs to security holes and telecom outages.
Unpredictable External Events
Finally, some of the trickiest risks are the ones that come from outside your four walls. You have very little, if any, direct control over these external events, but they can still wreak havoc on your operations, supply chains, and the market itself. You can't stop a hurricane, but good risk management in operations is all about being ready for one.
Common external risks include:
Natural Disasters: Things like floods, earthquakes, or wildfires can wipe out facilities and cripple logistics.
Supply Chain Shocks: The sudden failure of a critical supplier can bring your entire production line to a standstill.
Regulatory Changes: A new government regulation can force you to make expensive changes to your products or how you do business.
Political Instability: Trade wars, regional conflicts, or political turmoil can create a completely unpredictable environment.
To tie this all together, here’s a quick summary of the four pillars and what they look like in practice.
The Four Pillars of Operational Risk
Pillar | Description | Common Risk Examples |
|---|---|---|
People | Risks originating from human actions, whether intentional or unintentional. | Employee error, internal fraud, lack of training, unethical behavior, and skills gaps. |
Processes | Risks caused by failed or inadequate internal procedures, controls, and systems. | Poorly designed workflows, weak quality control, failed compliance, and lack of oversight. |
Systems | Risks arising from failures in technology, including hardware, software, and networks. | IT system outages, software bugs, data breaches, hardware failures, and cybersecurity attacks. |
External Events | Risks stemming from events outside the organization’s control. | Natural disasters, regulatory changes, supplier failures, political unrest, and economic downturns. |
By thinking about your operations through the lens of these four categories, you can start to systematically identify where your biggest vulnerabilities lie and build a more resilient business from the ground up.
Implementing the Operational Risk Management Lifecycle
Effective risk management isn't a one-and-done project. It’s a living, breathing cycle that constantly reinforces your operations.
Picture a ship captain navigating choppy seas. They don't just check the weather once and lock in a course. They're always on the lookout for potential storms, judging their severity, adjusting the sails, and keeping a close eye on the radar. That's how you should approach risk management in operations.
This cyclical method turns risk management from a theoretical exercise into a practical playbook. By moving through a structured lifecycle—Identification, Assessment, Mitigation, and Monitoring—you build a resilient system for handling whatever comes your way.
Stage 1: Identification – Uncovering Hidden Threats
You can't manage a risk you don't know exists. This first stage is all about proactive investigation—hunting for potential threats before they can cause any real damage. Think of it less like fortune-telling and more like detective work, using a few trusty tools to shine a light on vulnerabilities in your people, processes, and systems.
Here are a few practical ways to uncover these hidden risks:
Workshops and Brainstorming: Get teams from different departments in a room to talk through "what if" scenarios. You'd be surprised what comes to light when finance, IT, and production compare notes.
Process Mapping: Drawing out a workflow from start to finish is a fantastic way to spot bottlenecks, single points of failure, or gaps in your controls.
Incident Analysis: Dig into past failures and near-misses. They offer priceless clues about what can, and probably will, go wrong again if you don't address the root cause.
The goal here is to build a comprehensive risk register. This master list becomes the foundation for everything that follows.
Stage 2: Assessment – Prioritizing What Matters Most
With a long list of potential risks, the temptation is to tackle everything at once. That's a surefire path to getting overwhelmed. The assessment stage is where you bring order to the chaos by figuring out which risks truly deserve your attention.
The evaluation boils down to two simple questions:
Likelihood: How likely is this to actually happen?
Impact: If it does happen, how bad will the fallout be?
This infographic breaks down the core steps of a solid risk assessment, from gathering your intel to assigning a score.

As you can see, it's a straightforward flow: data collection informs a careful evaluation, which leads to a clear risk score.
A go-to tool for this is a risk matrix. It's a simple grid that plots likelihood against impact. Anything that lands in the high-likelihood, high-impact corner (usually colored red) is an immediate priority. Risks in the low-low corner (green) can be managed with less urgency. To keep your analysis organized, you can use our risk assessment form template to guide you.
Stage 3: Mitigation – Crafting Your Response Plan
Okay, you've prioritized your risks. Now what? The mitigation stage is all about creating an action plan. This is where you develop and roll out strategies to control, reduce, or even eliminate the threats you’ve identified.
There are four main ways to respond to a risk, often called the "4 Ts":
Treat: This is the most common approach. You implement new controls or change a process to reduce the risk’s likelihood or impact. A classic example is installing backup generators to treat the risk of a power outage.
Tolerate: For some minor risks, the cost of fixing them might be higher than the potential damage. In these cases, you might consciously decide to accept the risk and just deal with it if it happens.
Transfer: This means shifting the financial hit of a risk to someone else. Buying insurance is the perfect example—you transfer the financial risk of a fire or flood to the insurance company.
Terminate: If a risk is just too big to treat, tolerate, or transfer, your best move might be to stop the activity causing it. This could mean shutting down a product line or pulling out of a particular market.
The right mitigation strategy depends entirely on the specific risk and your organization's comfort level with it. There’s no universal answer; the goal is to make a conscious, informed decision for each major threat.
Stage 4: Monitoring – Keeping a Watchful Eye
Finally, operational risk management is not a "set it and forget it" task. The monitoring stage is what makes the whole cycle work over the long term. Your business will change, new risks will pop up, and old ones will evolve.
Good monitoring involves tracking Key Risk Indicators (KRIs)—specific metrics that act as early warning signals. For instance, a KRI for a potential data breach could be an unusual spike in failed login attempts.
By keeping an eye on these KRIs, you can take action before a risk turns into a full-blown crisis. This final stage feeds right back into identification, creating a continuous loop of improvement that makes your organization stronger and more resilient over time.
Confronting Modern Threats to Your Operations

While the core principles of risk management haven't changed, the threats themselves certainly have. The risks that kept managers awake a decade ago feel almost quaint compared to what we're up against today. To build real resilience, your approach to risk management in operations has to tackle the high-stakes challenges of the modern business world head-on.
Two major threats have stormed from the periphery right to the center of operational risk: cyber attacks and geopolitical instability. These aren't just abstract concerns for the C-suite; they have a direct, and often devastating, impact on day-to-day business. The key is learning how to connect these massive trends to your reality on the ground.
Cyber Threats Are Core Operational Failures
For a long time, cybersecurity was seen as a problem for the IT department to sort out. That mindset isn't just outdated—it’s dangerous. Today, a cyber incident is a core operational failure.
Think of a ransomware attack not just as data being locked, but as a factory floor grinding to a halt because its control systems are paralyzed. When digital systems run everything from inventory to logistics, a digital threat becomes a very physical one. A successful cyberattack can do far more than steal data; it can cripple your ability to make your product, deliver your service, and keep your promises to customers.
A data breach isn't just an IT issue; it's a breakdown in the operational process of safeguarding company assets. A system outage isn't just a technical glitch; it's a direct disruption to your revenue-generating activities.
The scale of this challenge is enormous. In fact, for the fourth year in a row, cyber incidents—including ransomware, data breaches, and IT outages—are ranked as the top global business risk. These events cause severe operational disruptions and deep reputational damage. If you want to dive deeper, you can explore the full findings of the global risk report to see the data for yourself.
Navigating Geopolitical Instability
The second major modern threat is the ripple effect of geopolitical instability. In a globally connected economy, an event happening thousands of miles away can hit your operations like a tidal wave. Trade disputes, regional conflicts, and political polarization are no longer just news headlines; they are direct operational hurdles.
Just look at the real-world impacts:
Sudden Supply Chain Collapse: A trade dispute can trigger new tariffs or outright bans on critical components overnight. Suddenly, you're forced into a costly and chaotic scramble to re-engineer your entire supply chain.
Regulatory Whiplash: Shifting political alliances can create a constantly changing and unpredictable regulatory landscape. Compliance becomes a moving target, and the risk of penalties skyrockets.
Market Access Issues: Political instability can make it difficult or even impossible to operate in certain countries, cutting you off from both customers and suppliers.
Managing this kind of risk requires a new level of awareness and agility. It's about more than just having a few backup suppliers; it’s about understanding the political and economic currents that could disrupt your entire operational model. Teams need to be ready for sudden shocks and have contingency plans they can roll out at a moment's notice.
A well-documented response plan is your best defense against these unpredictable events. When a crisis hits, a clear protocol ensures a coordinated, effective response, minimizing chaos and downtime. You can get a head start by using a detailed crisis management report form template to structure your incident reporting from day one.
Ultimately, effective risk management in operations today means building a strategy that is both digitally fortified and globally aware. By recognizing that a server vulnerability is just as much a threat as a blocked shipping lane, you can develop an operational framework that’s truly ready for the challenges of this decade and beyond. This proactive stance is what separates the businesses that merely survive from those that truly thrive.
Building a Resilient Business Continuity Plan
When a crisis hits, you don't have time to figure things out. Strong risk management in operations isn't just about dodging bullets; it’s about making sure your business can take a punch, get back up, and keep moving forward. This is where a rock-solid business continuity plan (BCP) becomes your playbook for survival.
Lots of people mix up business continuity with disaster recovery, but they’re two different beasts serving two very different functions.
Disaster Recovery (DR) is the IT-focused part of the puzzle. It’s all about getting the tech back online—rebooting servers, restoring data from backups, and making sure the digital plumbing works again. Think of it as recovering your systems.
Business Continuity (BC) is the whole shebang. It’s about keeping the entire business operational. This means making sure your team can work, your supply chain hasn't ground to a halt, and your customers are still being served, even if your main office is a no-go zone. It's about recovering your business.
A great DR plan might get your website back up after it crashes, but a BCP is what ensures your support team can still take calls and your warehouse can still get products out the door.
Pinpointing Your Most Critical Functions
You can't save everything at once, so the first step in any good BCP is triage. You need to figure out what's absolutely essential. This is done through a Business Impact Analysis (BIA), which is a methodical way to identify your mission-critical operations and understand the real-world damage if they go dark.
A BIA forces you to ask the hard questions:
Which processes bring in the most money?
What operations are non-negotiable for keeping our promises to customers?
Are there any legal or regulatory lines we absolutely cannot cross?
Which functions are the dominoes that would topple other critical parts of the business?
By getting clear answers here, you can set your priorities straight. This is where you'll define a Recovery Time Objective (RTO)—the absolute maximum downtime a process can handle—and a Recovery Point Objective (RPO), which is the maximum amount of data you can afford to lose. This analysis becomes the bedrock of your entire continuity strategy.
A Business Impact Analysis transforms your BCP from a generic document into a precise, actionable roadmap. It tells you exactly what to save first when the fire alarm goes off.
The cost of being caught flat-footed is mind-boggling. The United Nations Office for Disaster Risk Reduction estimates that when you factor in all the knock-on economic effects and ecosystem damage, disaster-related costs now blow past $2.3 trillion annually. That figure is nearly ten times higher than the direct damage estimates we usually hear about. You can read more about the global impact of disasters on UNDRR.org.
From Analysis to Actionable Strategy
Once the BIA has shown you what's most important, it's time to build your playbook. This means creating detailed, step-by-step procedures that tell your teams exactly what to do during and after a major disruption. A good BCP isn't a high-level theory; it's a practical guide for when things get chaotic. For a nuts-and-bolts approach, check out this essential business continuity plan checklist.
Your plan needs to spell out everything from alternate work arrangements and communication plans for staff and stakeholders to the exact steps for firing up backup systems or moving to a secondary location. Documenting these processes is what ensures a coordinated, calm response in a high-stress moment. To make this documentation easier, you can use a structured framework like our business continuity plan form template.
We've seen how this pays off in the real world. When a massive earthquake struck Japan, one car manufacturer got its assembly lines running again far faster than its competitors. Why? Because their BCP included a deep, granular understanding of their entire supply chain, right down to the smallest component suppliers. While everyone else was scrambling to find new vendors, this company was already activating its pre-vetted alternatives, ultimately grabbing more market share.
It's a perfect example of how proactive planning doesn't just prevent a catastrophe—it can turn a crisis into a competitive edge.
Embedding Risk Management into Your Company Culture

You can have the most sophisticated frameworks and detailed playbooks for risk management in operations, but they’ll just gather dust if your company culture isn’t on board. Real operational resilience doesn't come from a new software tool or a binder on a shelf; it's born from making risk awareness a shared responsibility that’s woven into the fabric of every team.
This is about a fundamental shift in mindset. It’s about moving risk management from a siloed, top-down function to something everyone owns. When you empower every employee to see themselves as a risk manager in their own role, you create a powerful, organization-wide sensor network for potential threats.
Creating Clear Accountability
So, how do you make this happen without creating chaos? A proven approach is the "three lines of defense" model. It’s a simple but effective way to clarify who owns what, spreading accountability logically across the business.
Here’s how it breaks down:
First Line: This is your front line. It includes the operational managers and their teams who are hands-on with the processes every day. They own and manage risk as part of their job.
Second Line: Think of this as the support and oversight crew. It’s your dedicated risk management and compliance functions that provide the tools, expertise, and guidance for the first line.
Third Line: This is your independent check-and-balance. The internal audit team provides objective assurance that the first two lines are actually working as they should.
This model dismantles the dangerous assumption that risk is "someone else's problem." It embeds ownership directly into the day-to-day workflow where it matters most.
A proactive risk culture is the ultimate competitive advantage. It’s what allows a company to not just survive uncertainty but to adapt and even thrive by making smarter, more informed decisions at every level.
Fostering a Proactive Environment
Building this culture really boils down to two things: ongoing training and transparent communication. Training can’t be a one-and-done annual presentation; it needs to be practical, role-specific, and continuous. And communication must be open and blame-free. People have to feel safe raising their hand to flag a potential issue without fear of reprisal.
Despite the obvious benefits, getting this cultural piece right is where many organizations fall short. A shocking 87% of risk professionals feel that risk management processes are not widely accepted within their companies, according to research shared by ProcurementTactics.com. That statistic reveals a huge gap between policy and practice.
Ultimately, a company that truly values proactive risk management is one that empowers its people. When your team is trained, accountable, and engaged, they become your single greatest asset in building a resilient operation. For companies looking to bring in the right leaders, an operational risk manager job application template can be a great starting point to define the skills that really matter.
Frequently Asked Questions
What Is the First Step in an Operational Risk Program?
The very first move—before you even think about frameworks or tools—is to get executive sponsorship. Without leadership championing the effort, any risk program is dead in the water. Once you have that backing, assemble a team with people from different departments.
With your team in place, your next step is a high-level Business Impact Analysis (BIA). This helps you pinpoint the most critical processes that keep your business running. Focusing here first gets you early wins and proves the program's value to everyone else.
How Does Operational Risk Differ from Financial Risk?
Think of it this way: financial risk is about the money itself—things like credit defaults, market swings, or currency fluctuations. Risk management in operations, on the other hand, deals with the engine that makes the money: your internal processes, people, and systems.
A bad investment is a financial risk. The entire trading platform crashing because of a server failure or a sleepy employee hitting the wrong button? That's a classic operational risk. While the outcome is often financial, the cause is a breakdown in how the business runs.
Understanding the distinction is key. Financial risk is about managing capital, while operational risk is about managing the machinery that generates that capital. One cannot be effective without the other.
How Often Should We Review Our Risk Assessments?
Risk assessments aren't a "set it and forget it" activity. A good rule of thumb is to conduct a full, formal review at least annually.
But don't wait a whole year for your biggest threats. Your risk register and the plans for mitigating your most severe risks should get a closer look, probably quarterly.
And remember, major business changes should always trigger an immediate review. If you’re launching a new product line, expanding to a new country, or rolling out a new ERP system, you need to assess the new operational risks that come with it right away.
Ready to transform your risk management from a static process into an intelligent, autonomous workflow? Nolana deploys AI agents that can plan, execute, and detect risks across your operations. Discover how our platform can give you unparalleled visibility and control. Learn more at https://nolana.com.
Want early access?
© 2026 Nolana Limited. All rights reserved.
Leroy House, Unit G01, 436 Essex Rd, London N1 3QP
Want early access?
© 2026 Nolana Limited. All rights reserved.
Leroy House, Unit G01, 436 Essex Rd, London N1 3QP
Want early access?
© 2026 Nolana Limited. All rights reserved.
Leroy House, Unit G01, 436 Essex Rd, London N1 3QP
Want early access?
© 2026 Nolana Limited. All rights reserved.
Leroy House, Unit G01, 436 Essex Rd, London N1 3QP